Secure Access Service Edge (SASE): The future of network security
September 23, 2023
Keep your software up to date: A simple way to improve your cybersecurity
September 25, 2023
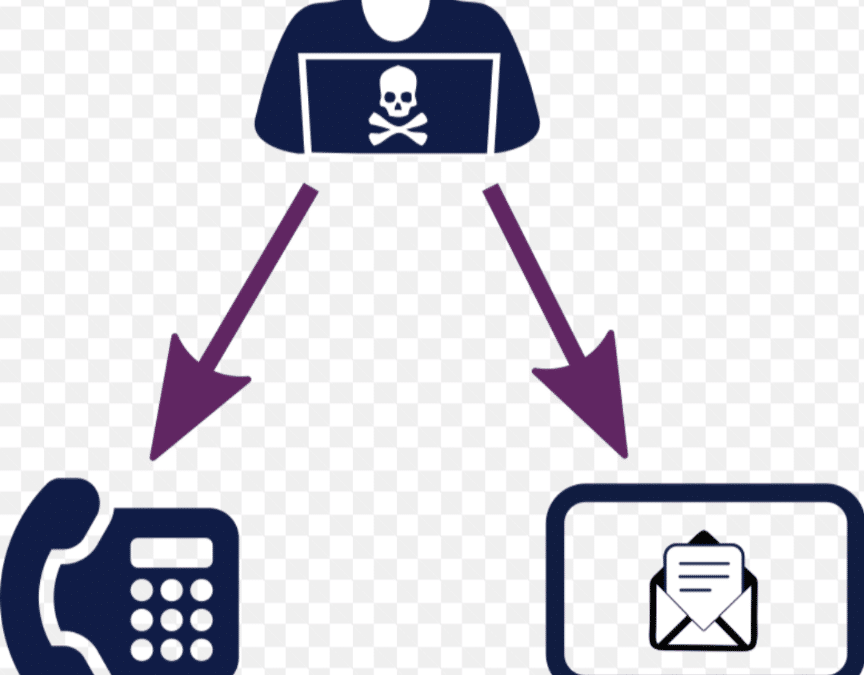
Whaling is a type of phishing attack that targets high-profile individuals, such as CEOs, CFOs, and other executives. Whaling attacks are often very sophisticated and personalized, and they can be very difficult to detect.
How whaling attacks differ from other phishing attacks
Whaling attacks differ from other phishing attacks in a number of ways. First, whaling attacks are typically more targeted. The attackers will research the victim carefully and tailor the attack to their specific interests and vulnerabilities. Second, whaling attacks are often more personalized. The attackers may use the victim’s name in the email subject line or greeting, or they may reference a specific project or deal that the victim is working on. Third, whaling attacks often involve larger financial stakes. The attackers may be trying to trick the victim into authorizing a large wire transfer or into revealing sensitive financial information.
How whaling attacks are carried out
Whaling attacks are typically carried out by sending a phishing email to the victim that appears to be from a trusted source, such as the victim’s boss, customer, or vendor. The email may contain a link to a malicious website or an attachment that contains malware. If the victim clicks on the link or opens the attachment, their computer can be infected with malware or their personal information can be stolen.
In addition to phishing emails, whaling attackers may also use social engineering techniques to trick the victim. For example, the attackers may call the victim and pose as a trusted colleague or vendor. They may also try to gain the victim’s trust by sending them a series of emails that build rapport.
Examples of whaling attacks
Some notable examples of whaling attacks include:
– In 2015, hackers targeted Sony Pictures Entertainment by sending phishing emails to employees that appeared to be from the company’s CEO. The emails contained a link to a malicious website that infected the company’s network with malware. The attack resulted in the theft of a large amount of data, including sensitive employee and customer information.
– In 2016, hackers targeted Bangladesh Bank by sending phishing emails to employees that appeared to be from the Federal Reserve Bank of New York. The emails contained instructions for wiring money to bank accounts controlled by the attackers. The bank lost over $100 million in the attack.
– In 2017, hackers targeted the CEO of Uber by sending him a phishing email that appeared to be from security researcher. The email contained a link to a malicious website that infected the CEO’s computer with malware. The attackers then used the malware to steal the CEO’s login credentials and gain access to the company’s network.
How to protect yourself from whaling attacks
There are a number of things that organizations and individuals can do to protect themselves from whaling attacks, including:
– Educate employees about whaling attacks. Employees should be trained on how to identify and avoid phishing attacks, including whaling attacks. This training should be ongoing and should cover the latest threats and attack vectors.
– Implement strong security policies and procedures. Organizations should have strong security policies and procedures in place to help protect their systems and data from whaling attacks. These policies and procedures should be regularly reviewed and updated to ensure that they are effective against the latest threats.
– Use security software and solutions. Organizations should use security software and solutions to help detect and prevent whaling attacks. Security software and solutions can help to protect against a variety of threats, such as malware and phishing attacks.
– Be careful about what emails you open and what links you click on. Individuals should be careful about what emails they open and what links they click on. If you receive an email from someone you don’t know, or if the email seems suspicious, don’t open it. If you are unsure about an email, contact the sender directly to verify that it is legitimate.
Whaling is a serious threat to organizations and individuals. By taking the steps outlined above, organizations and individuals can help to protect themselves from whaling attacks.
It is important to note that whaling attacks are becoming increasingly common and sophisticated. Attackers are constantly developing new techniques to exploit human psychology and trick victims into falling for their attacks. This makes it more important than ever to be aware of the risks and to take steps to protect yourself.
If you are ever unsure about an email or a phone call, it is always better to err on the side of caution and not engage. You can always contact the sender or caller directly to verify their identity.
#whaling #phishing #cybersecurity