Keep your software up to date: A simple way to improve your cybersecurity
September 25, 2023
Security software: A must-have for SMBs
September 28, 2023Social engineering attacks are a type of cyberattack that exploits human psychology to trick people into revealing confidential information or performing actions that compromise security. Social engineering attacks can be carried out in person, over the phone, or via email and social media.
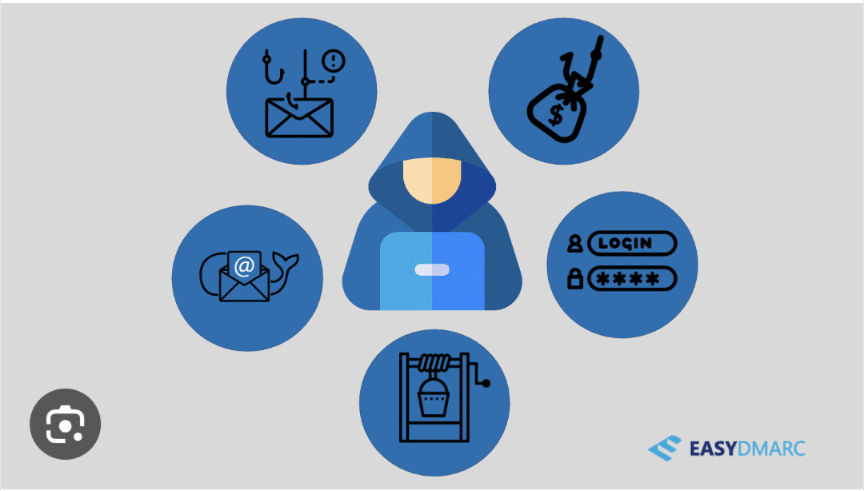
Social engineering attacks are one of the most common and successful types of cyberattacks because they prey on human vulnerabilities, such as trust, curiosity, and fear. Hackers use a variety of social engineering techniques to trick people, such as:
- Phishing: Phishing attacks involve sending emails or text messages that appear to be from a legitimate source, such as a bank or credit card company. The emails or text messages may contain a link to a malicious website or an attachment that contains malware.
- Pretexting: Pretexting attacks involve creating a false scenario to gain the victim’s trust. For example, a hacker may call a victim and claim to be from their bank’s fraud department. The hacker may then ask the victim for their account number and PIN.
- Baiting: Baiting attacks involve leaving a malicious device or file in a public place, such as a coffee shop or library. The device or file may be labeled in a way that makes it appear legitimate, such as “USB Flash Drive” or “Important Document.” If a victim picks up the device or file and opens it, their computer could be infected with malware.
- Quid pro quo: Quid pro quo attacks involve offering something of value in exchange for information or access. For example, a hacker may call a victim and offer to help them with their computer problems. In exchange, the hacker may ask the victim for their remote access credentials.
- Tailgating: Tailgating attacks involve following a victim into a secure area, such as an office building or data center. Hackers often use tailgating attacks to gain access to physical systems and data.
How to protect yourself from social engineering attacks
There are a number of things you can do to protect yourself from social engineering attacks, including:
- Be suspicious of unsolicited emails and phone calls. If you receive an email or phone call from someone you don’t know, be wary of clicking on any links or opening any attachments.
- Verify the identity of the sender. If you are unsure about the identity of the sender, try to contact the organization they claim to be from directly. For example, if you receive an email from your bank, call your bank’s customer service number to verify that the email is legitimate.
- Be careful about what information you share. Only share personal information with websites and apps that you trust. Be wary of sharing your personal information on social media.
- Use strong passwords and multi-factor authentication (MFA). Strong passwords are at least 12 characters long and include a mix of upper and lowercase letters, numbers, and symbols. MFA adds an extra layer of security by requiring you to enter a code from your phone in addition to your password when logging in to accounts.
- Keep your software up to date. Software updates often include security patches that can fix vulnerabilities that hackers can exploit.
Social engineering attacks are a serious threat to cybersecurity. By following the tips above, you can help to protect yourself from social engineering attacks and keep your data safe.
Additional tips
- Educate yourself about social engineering attacks. The more you know about social engineering attacks, the less likely you are to fall victim to one.
- Be aware of your surroundings. Pay attention to who is around you when you are entering a secure area or using a public computer.
- Report suspicious activity. If you think you may be a victim of a social engineering attack, report it to your IT department or to the organization that was targeted.
#socialengineering #cybersecurity #securitytips