Cyber Insurance Coverage Becoming More Restrictive and Premiums Increasing: How it Affects SMBs
October 17, 2023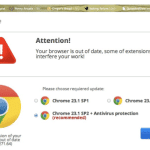
The latest version of the fake browser update scam: What you need to know
October 20, 2023Zero trust security is a security model that assumes that no user or device can be trusted by default. This model requires all users and devices to be authenticated and authorized before they are granted access to any resources.
Zero trust security is becoming increasingly popular as organizations move to the cloud and adopt new technologies such as remote work and the Internet of Things (IoT). These changes have created a more complex and distributed threat landscape, making it more difficult to protect traditional security perimeters.
What are the benefits of zero trust security?
Zero trust security offers a number of benefits, including:
- Improved security: Zero trust security can help to protect organizations from a variety of threats, including data breaches, malware attacks, phishing attacks, and insider threats.
- Reduced risk: Zero trust security can help organizations to reduce their risk of compliance violations and financial losses.
- Increased agility: Zero trust security can help organizations to be more agile and responsive to change.
- Improved user experience: Zero trust security can provide a more seamless and user-friendly experience for employees.
How to implement zero trust security
To implement zero trust security, organizations need to:
- Identify their critical assets and data. What information is most important to the organization and needs to be protected?
- Understand the risks to those assets and data. What are the threats that could impact those assets and data?
- Implement security controls to mitigate those risks. What security controls can be put in place to protect those assets and data from those threats?
- Continuously monitor and update their security controls. The threat landscape is constantly evolving, so it is important to regularly review and update security controls to ensure that they are effective.
Here are some specific examples of zero trust security controls:
- Multi-factor authentication (MFA): MFA requires users to provide two or more factors of authentication before they are granted access to resources. This can help to prevent unauthorized access, even if an attacker has compromised a user’s password.
- Microsegmentation: Microsegmentation divides networks into smaller segments and restricts traffic between those segments. This can help to prevent attackers from moving laterally within a network if they are able to gain access to one segment.
- Context-aware access control: Context-aware access control grants access to resources based on the user’s identity, device, location, and other factors. This can help to prevent unauthorized access to resources, even if the user has been authenticated.
Zero trust security for different industries
Zero trust security can be applied to organizations in all industries. However, there are some specific considerations for different industries.
Zero trust security is a journey, not a destination. It is important to start small and gradually implement zero trust security controls over time.
For example, organizations in the financial industry need to be particularly concerned with protecting customer data. Zero trust security can help financial organizations to protect this data from unauthorized access and breaches.
Organizations in the healthcare industry need to be particularly concerned with protecting patient data. Zero trust security can help healthcare organizations to protect this data from unauthorized access and breaches.
Zero trust security and the future of cybersecurity
Zero trust security is the future of cybersecurity. It is a security model that is well-suited to the modern threat landscape.
Zero trust security can help organizations to protect their critical assets and data from a variety of threats, including data breaches, malware attacks, phishing attacks, and insider threats.
Organizations that are looking to improve their security posture should consider implementing zero trust security.
There is no one-size-fits-all approach to zero trust security. The specific controls that are implemented will vary depending on the organization’s specific needs and requirements.
It is important to get buy-in from all levels of the organization before implementing zero trust security. Zero trust security requires a change in mindset, and it is important that everyone understands the benefits and how it will work.
Zero trust security is a powerful security model that can help organizations to protect themselves from a variety of threats. It is a journey, not a destination, but it is one that is worth taking.
#ZeroTrustSecurity #Cybersecurity #InformationSecurity #CloudSecurity #NetworkSecurity