Multi-Stage Phishing Attacks: A Multifaceted Threat
November 22, 2023
Shielding Your Financial Fortress: Protecting Your Bank Account Passwords from AI-Powered Threats
November 24, 2023In the ever-evolving landscape of cybersecurity, Mac users have long enjoyed a reputation for being less susceptible to malware attacks compared to their Windows counterparts. However, this perceived safety net is constantly challenged by cunning cybercriminals devising new tactics to exploit vulnerabilities and infiltrate unsuspecting systems. A recent campaign known as ClearFake exemplifies this growing threat, targeting macOS systems with fake browser updates that harbor the insidious Atomic Stealer malware.
ClearFake’s Cunning Disguise
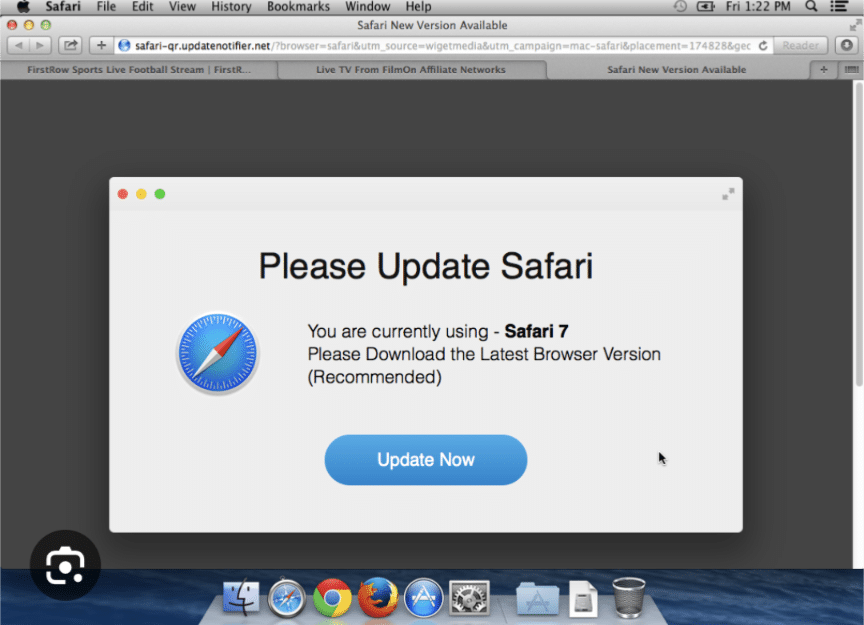
ClearFake’s modus operandi revolves around exploiting the trust users have in legitimate websites. By compromising these sites and injecting them with malicious code, attackers can seamlessly blend their fake browser update prompts into the genuine user experience. When a user visits one of these infected sites, a pop-up notification appears, mimicking the genuine browser update prompts that users have become accustomed to seeing.
This deceptive approach can easily ensnare unsuspecting users, who may instinctively click on the prompt to initiate the update process. Once this action is taken, users are directed to a meticulously crafted fake browser update page that bears all the hallmarks of authenticity. The page displays a download button labeled with the name of the affected browser, further reinforcing the illusion of legitimacy. Upon clicking the download button, users unwittingly unleash the Atomic Stealer malware onto their Mac systems.
Atomic Stealer: A Stealthy Data-Exfiltration Trojan
Atomic Stealer is not merely a harmless inconvenience; it is a sophisticated and stealthy malware designed to exfiltrate sensitive information from infected devices. This malware operates silently in the background, meticulously gathering a wide range of valuable data, including:
- Passwords stored in browsers
- Autofill information
- User account credentials
- Browser cookies
- Keychain data
- Wallet information
With this trove of stolen data in their possession, attackers can unleash a range of malicious activities, such as:
- Financial fraud
- Identity theft
- Targeted attacks
- Sale of stolen data on dark web marketplaces
Defending Your Mac from ClearFake and Atomic Stealer
In the face of this evolving threat, Mac users must adopt a proactive approach to cybersecurity, implementing measures to safeguard their systems and sensitive information:
- Vigilance is Key: Exercise caution when encountering unsolicited pop-ups or notifications urging you to update your browser. Always verify the authenticity of the source before clicking on any links or buttons.
- Official Sources for Updates: When seeking browser updates, always check for official announcements from the browser’s developer. Visit the browser’s official website or app store to download legitimate updates.
- Robust Security Solutions: Employ a reliable and up-to-date security software capable of detecting and blocking malware. Regularly update your security software to ensure it maintains the latest protection against emerging threats.
- Safe Browsing Habits: Avoid visiting untrusted or suspicious websites. Refrain from clicking on links or attachments in emails from unknown senders.
- Software Updates: Regularly update your macOS operating system and applications to ensure they have the latest security patches and bug fixes.
By adhering to these essential precautions, you can significantly reduce your risk of falling victim to ClearFake and its nefarious payload, Atomic Stealer. Remember, cybersecurity is an ongoing endeavor, requiring constant vigilance and proactive measures to stay ahead of ever-evolving threats.
#MacSecurity #FakeBrowserUpdates #ClearFakePrevention #AtomicStealerMitigation #CybersecurityExpertise