AI Security: Shielding the Future of AI from Cyber Threats
November 27, 2023
Navigating the Digital Landscape with Confidence: Strengthening Password Policies
November 30, 2023Man in the Middle Attacks: How to Protect Yourself
In today’s digital world, we are constantly communicating with others online. We share sensitive information, such as our login credentials and financial details, over the internet without thinking twice. However, this makes us vulnerable to man-in-the-middle (MITM) attacks.
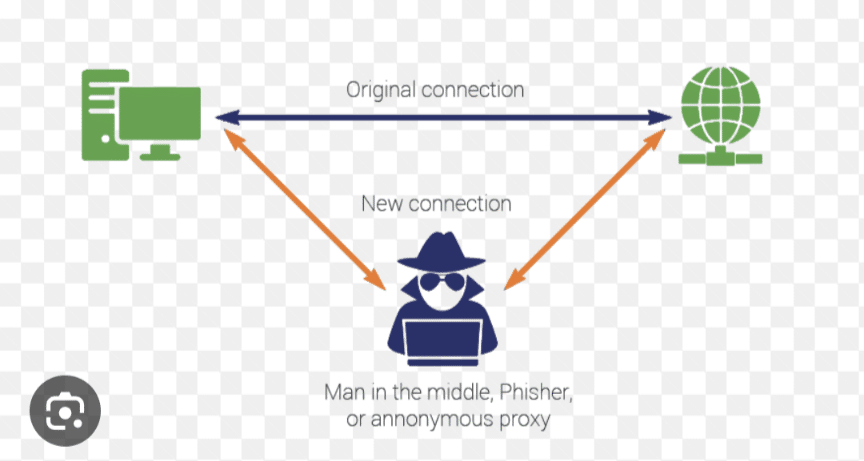
A MITM attack is a type of cyberattack where an attacker secretly intercepts and relays communications between two parties who believe they are communicating directly with each other. The attacker can then eavesdrop on the conversation, steal sensitive information, or even alter the data being exchanged.
How MITM Attacks Work
MITM attacks can be carried out in a variety of ways, but they all involve the attacker positioning themselves between the two parties who are communicating. This can be done by creating a fake Wi-Fi hotspot, tricking the victim into clicking on a malicious link, or exploiting a vulnerability in the software that the victim is using.
Once the attacker is positioned in the middle, they can intercept and decrypt all of the traffic between the two parties. This allows them to steal sensitive information, such as login credentials, credit card numbers, and social security numbers. They can also alter the data being exchanged, which can have serious consequences. For example, an attacker could redirect a victim to a fake website that looks like the real website of their bank. If the victim enters their login credentials into the fake website, the attacker can steal them.
How to Protect Yourself from MITM Attacks
There are a number of things you can do to protect yourself from MITM attacks:
- Use strong passwords and enable two-factor authentication (2FA). This will make it more difficult for attackers to guess your login credentials.
- Be careful about using public Wi-Fi networks. Public Wi-Fi networks are often unencrypted, which means that anyone on the network can intercept your traffic. If you must use public Wi-Fi, use a VPN to encrypt your traffic.
- Be careful about clicking on links in emails. Malicious links can be used to redirect you to fake websites that can steal your information.
- Keep your software up to date. Software updates often include security patches that fix vulnerabilities that attackers can exploit.
- Use a firewall. A firewall can help to block unauthorized traffic from reaching your computer.
- Use a VPN. A VPN encrypts all of your internet traffic, which makes it more difficult for attackers to intercept it.
Additional Tips
In addition to the tips above, here are a few more things you can do to stay safe online:
- Be aware of your surroundings. If you are using a public computer, make sure that no one can see your screen.
- Don’t share sensitive information over the internet unless you are sure that the website is secure. Look for the “https://” prefix in the URL and make sure that the website has a valid SSL certificate.
- Be careful about what you download from the internet. Malicious software can be used to launch MITM attacks. Only download software from trusted sources.
MITM attacks are a serious threat to our online security. By following the tips in this blog post, you can help to protect yourself from these attacks.
#mitm #cybersecurity #maninthemiddle #protectyourself #online