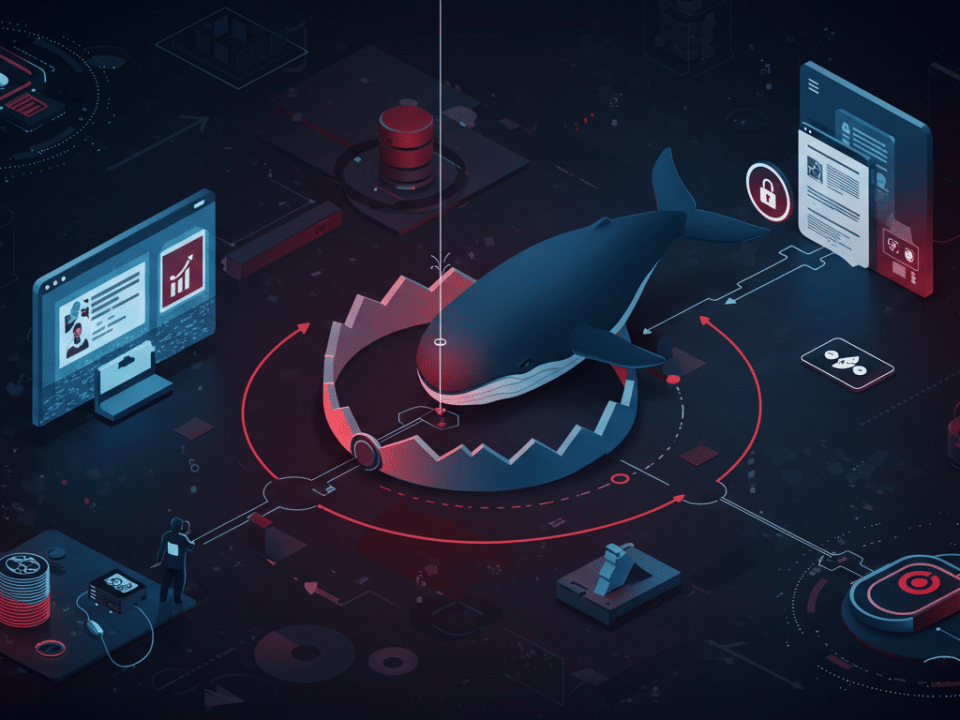
Big Catch, Big Threat: Understanding Whale Phishing
March 13, 2025
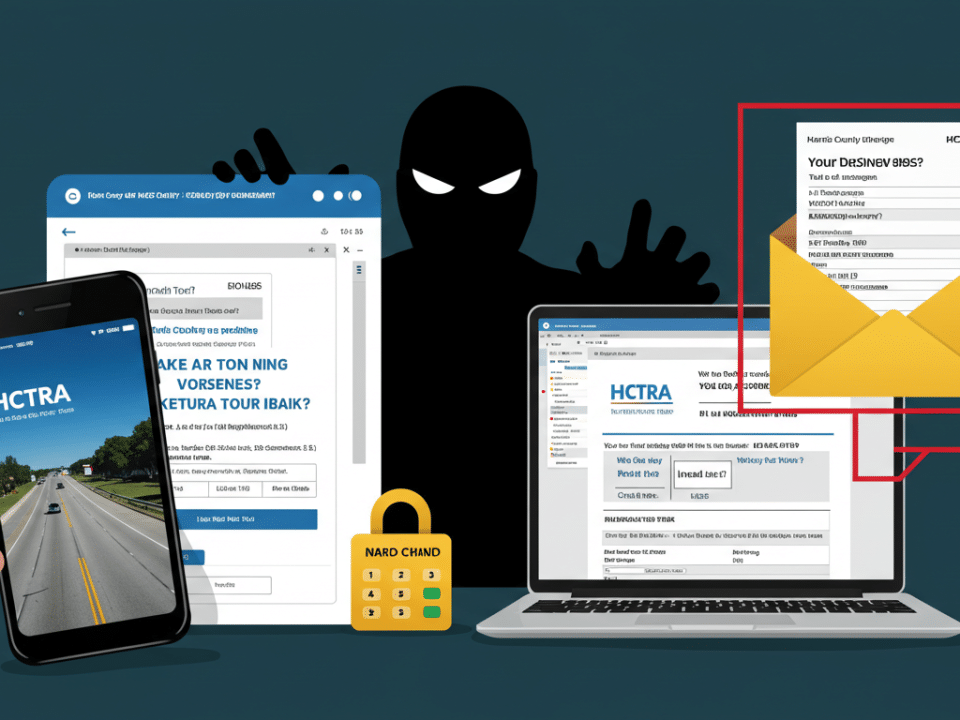
Fake HCTRA Scams Target Houston Businesses
March 16, 2025Shielding Your Business: Understanding Network Security
In today’s digital landscape, network security is no longer a luxury—it’s a necessity, especially for small to medium businesses (SMBs). For businesses in Houston, Texas, and beyond, a robust network security strategy is vital to protect sensitive data, maintain operational continuity, and build customer trust. But what exactly is network security?
At its core, network security encompasses the policies, practices, and technologies designed to protect the usability and integrity of your network and data. It’s about preventing unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. In the context of SMBs, this means safeguarding everything from customer data and financial records to intellectual property and employee information.
Steps to Achieve Robust Network Security for SMBs
Establishing effective network security doesn’t have to be overwhelming. Here’s a breakdown of actionable steps SMBs can take:
1. Conduct a Comprehensive Network Assessment:
- Begin by understanding your current network infrastructure. Identify potential vulnerabilities, including outdated software, weak passwords, and unsecured devices.
- Tools like network scanners can help map your network and pinpoint security gaps.
- A professional assessment from a company like Krypto IT can provide a detailed report and actionable recommendations.
2. Implement a Strong Firewall:
- A firewall acts as a barrier between your trusted internal network and untrusted external networks, such as the internet.
- Configure your firewall to filter incoming and outgoing traffic based on predefined security rules.
- Consider next-generation firewalls (NGFWs) for advanced threat detection and prevention capabilities.
3. Secure Your Wi-Fi Network:
- Ensure your Wi-Fi network is protected with a strong, unique password and WPA2 or WPA3 encryption.
- Implement a guest network for visitors to separate their traffic from your business’s critical data.
- Consider hiding your network’s SSID to make it less visible to potential attackers.
4. Regularly Update Software and Systems:
- Software updates often include critical security patches that address known vulnerabilities.
- Establish a schedule for updating operating systems, applications, and firmware.
- Enable automatic updates whenever possible to minimize the risk of human error.
5. Implement Strong Password Policies and Multi-Factor Authentication (MFA):
- Enforce the use of strong, unique passwords that are regularly changed.
- Implement MFA to add an extra layer of security, requiring users to provide multiple forms of verification before accessing sensitive data.
- Password management tools can help employees create and store strong passwords securely.
6. Educate Employees on Cybersecurity Best Practices:
- Human error is a leading cause of security breaches.
- Conduct regular cybersecurity training to educate employees on phishing scams, social engineering tactics, and safe browsing habits.
- Foster a culture of security awareness throughout your organization.
7. Implement Endpoint Protection:
- Install antivirus and anti-malware software on all devices connected to your network.
- Use endpoint detection and response (EDR) solutions for advanced threat monitoring and incident response.
- Ensure that all devices are regularly scanned for malware and vulnerabilities.
8. Regular Data Backups and Disaster Recovery:
- Implement a robust backup strategy to protect your critical data from loss due to hardware failure, cyberattacks, or natural disasters.
- Store backups in a secure, offsite location or in the cloud.
- Develop a disaster recovery plan to ensure business continuity in the event of a security incident.
9. Intrusion Detection/Prevention Systems (IDS/IPS):
- IDS monitors network traffic for suspicious activity and alerts administrators.
- IPS goes a step further by automatically blocking or preventing malicious traffic.
- These systems provide an extra layer of defense against sophisticated cyber threats.
Best Practices for Protecting SMBs:
- Regular Security Audits: Conduct periodic security audits to identify and address vulnerabilities.
- Principle of Least Privilege: Grant users only the permissions they need to perform their job duties.
- Incident Response Plan: Have a clear plan in place for how to respond to a security incident.
- Use a VPN: A Virtual Private Network provides an encrypted connection for remote workers.
- Stay Informed: Keep up to date with the latest cybersecurity threats and trends.
Secure Your Houston Business with Krypto IT
Don’t leave your business vulnerable to cyber threats. At Krypto IT, we specialize in providing comprehensive cybersecurity solutions for SMBs in Houston, Texas. Our expert team can help you assess your network security, implement effective safeguards, and ensure your business is protected.
Contact us today for a free consultation and let us help you fortify your network security.
Ready to strengthen your network security? Contact Krypto IT today for a free cybersecurity consultation! Let us help you protect your business from evolving cyber threats.
#CyberSecurity #NetworkSecurity #SMBsecurity #HoustonTech #KryptoIT #ITsecurity #DataProtection #CyberAwareness #TechTips #SmallBusinessSecurity #TexasBusiness