Hashing vs. Encryption: Unlocking the Key Differences in Cybersecurity
December 28, 2024
Data Leakage: Understanding the Silent Threat to Your Information
December 31, 2024In today’s threat landscape, passwords alone are no longer enough to protect your valuable online accounts. Cybercriminals are becoming increasingly sophisticated in their attacks, employing methods like phishing, credential stuffing, and brute-force attacks to compromise user accounts. That’s where multi-factor authentication (MFA) comes in – a critical security measure that adds layers of protection beyond just a username and password.
As your trusted cybersecurity partner, Krypto IT is committed to educating you on the most effective security practices. This blog post will delve into the world of MFA, explaining what it is, how it works, and providing practical guidance on implementing it to safeguard your digital life.
What is Multi-Factor Authentication (MFA)?
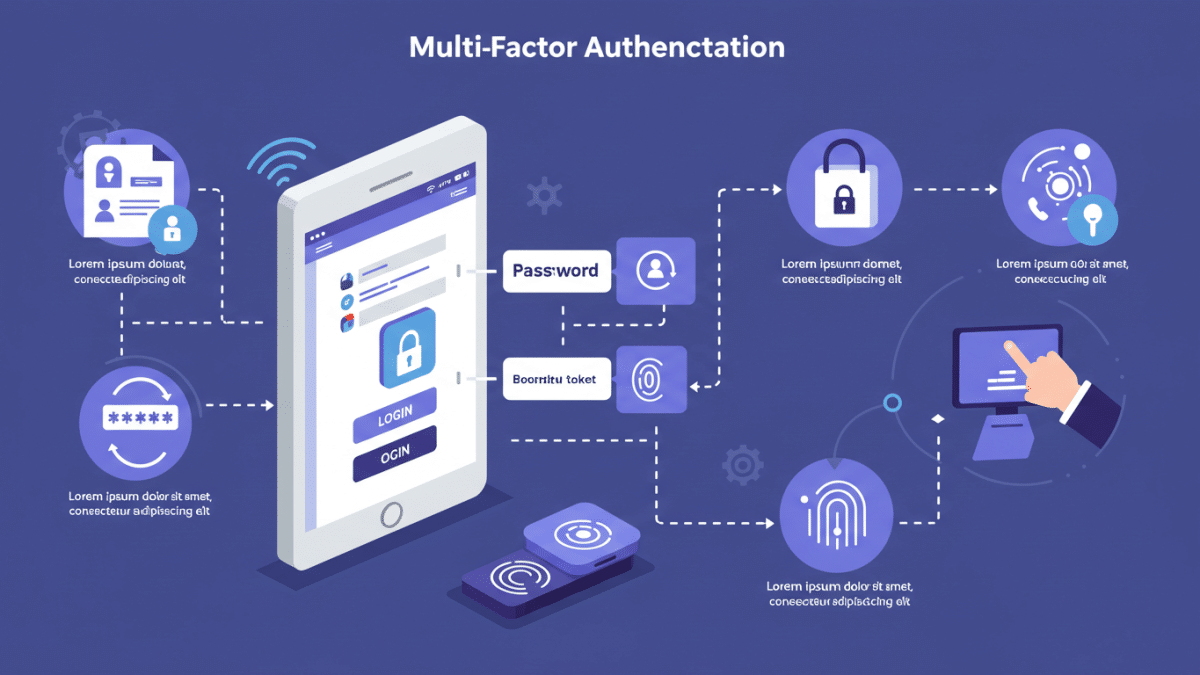
Multi-factor authentication (MFA) is a security process that requires users to provide two or more distinct authentication factors to verify their identity before granting access to an account or system. These factors are based on different categories of authentication credentials, ensuring that even if one factor is compromised, the attacker still faces additional barriers.
The Three Main Categories of Authentication Factors:
- Something You Know: This is typically a password, PIN, or the answer to a security question. It’s information that only the user should know.
- Something You Have: This is a physical object in the user’s possession, such as a smartphone, security token, or smart card.
- Something You Are: This refers to a biometric characteristic unique to the user, such as a fingerprint, facial recognition, or voice recognition.
How Does MFA Work?
When MFA is enabled, the login process involves multiple steps:
- First Factor: The user typically enters their username and password (something you know).
- Second Factor (and potentially more): The system then prompts the user to provide an additional factor, such as:
- One-Time Passcode (OTP): A time-sensitive code generated by an authenticator app or sent via SMS.
- Push Notification: An approval request sent to a registered mobile device.
- Biometric Verification: A fingerprint scan, facial recognition scan, or voice match.
- Security Key: A physical USB or NFC device that provides cryptographic authentication.
Only after successfully providing all required factors is the user granted access.
Why is MFA so Important?
MFA significantly enhances security by making it much harder for attackers to gain unauthorized access, even if they obtain a user’s password. If one factor is compromised, the attacker still needs to bypass the other factor(s), which is significantly more difficult.
Benefits of Implementing MFA:
- Reduced Risk of Account Takeover: MFA is highly effective in preventing unauthorized access due to stolen or weak passwords.
- Enhanced Data Protection: It adds an extra layer of security for sensitive data and systems.
- Compliance with Regulations: Many industry regulations and compliance standards (e.g., PCI DSS, HIPAA, GDPR) require or strongly recommend MFA.
- Increased User Trust: Demonstrates a commitment to security and helps build user confidence.
Best Practices, Policies, and Procedures for Implementing MFA
1. Planning and Policy:
- Develop an MFA Policy: Create a formal policy that mandates MFA for all users and systems, specifying the required authentication factors and acceptable methods.
- Risk Assessment: Identify high-risk accounts and systems that require the strongest MFA protection.
- User Education: Train users on the importance of MFA, how to use it properly, and what to do if they encounter issues.
- Choose Appropriate Factors: Select authentication factors that are appropriate for your organization’s security needs and user base. Consider factors like usability, cost, and security level.
2. Implementation:
- Phased Rollout: Implement MFA in phases, starting with high-risk users and systems before expanding to the entire organization.
- Integration with Existing Systems: Integrate MFA with your existing identity and access management (IAM) systems.
- User Enrollment: Provide a seamless and user-friendly process for users to enroll in MFA and register their authentication devices.
- Fallback Mechanisms: Establish procedures for users who lose their authentication devices or encounter other issues accessing their accounts.
3. Monitoring and Maintenance:
- Monitor MFA Activity: Track MFA usage, failed login attempts, and any suspicious activity.
- Regularly Review and Update: Periodically review your MFA policy and procedures to ensure they remain effective and aligned with evolving threats.
- Stay Informed: Keep up-to-date on the latest MFA technologies and best practices.
4. Procedures for Dealing with MFA Issues
- Lost or Stolen Devices: Have clear instructions for users on what to do if they lose their smartphone or security token. This typically includes immediately contacting IT support to disable the device and enroll a new one.
- Account Lockout: Have policies in place to handle users who get locked out after failed authentication. This may involve a set waiting period or contacting IT support for assistance.
- Bypass Requests: Establish procedures for handling requests to bypass MFA in exceptional circumstances. These requests should be carefully reviewed and approved only when absolutely necessary.
- Support and Troubleshooting: Provide users with readily available support and troubleshooting resources to address any MFA-related issues.
Krypto IT: Your Partner in Strong Authentication
Implementing multi-factor authentication is a crucial step in strengthening your organization’s cybersecurity posture. It’s a powerful deterrent against unauthorized access and a vital component of a comprehensive security strategy.
Krypto IT can help you navigate the complexities of MFA implementation. Our experts can assist you in developing an MFA policy, selecting appropriate authentication factors, integrating MFA with your existing systems, and providing ongoing support and training. Contact us today for a free consultation and let us help you move beyond passwords to a more secure future.
Don’t rely on passwords alone. Embrace multi-factor authentication. Be secure with Krypto IT.
#Cybersecurity #MultiFactorAuthentication #MFA #TwoFactorAuthentication #2FA #Authentication #InfoSec #CyberDefense #PasswordSecurity #DataProtection #DigitalSecurity #KryptoIT #CyberAwareness #SecurityBestPractices #OnlineSafety #TechSecurity