Endpoint Security for SMBs: Best Practices, Tips, and Recommendations
November 3, 2023
Cybersecurity for Beginners: How to Stay Safe in the Digital World
November 5, 2023Incident response (IR) and forensics are two critical components of cybersecurity. IR is the process of detecting, responding to, and recovering from a cybersecurity incident, such as a data breach or ransomware attack. Forensics is the process of investigating a cybersecurity incident to collect and analyze evidence.
IR and forensics are often closely intertwined. For example, IR teams may need to collect and preserve evidence in order to effectively respond to an incident. Similarly, forensics teams may need to work closely with IR teams to understand the context of an incident and to identify the root cause.
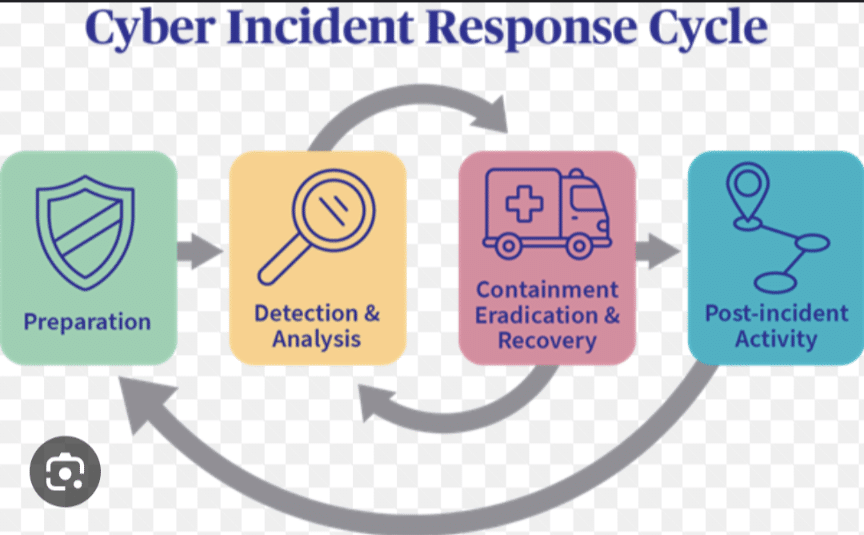
Incident Response
The IR process typically consists of the following steps:
- Identification: Identify the incident and assess its severity. This may involve gathering information from logs, security tools, and witnesses.
- Containment: Contain the incident to prevent further damage. This may involve isolating affected systems, disabling compromised accounts, and blocking malicious traffic.
- Eradication: Eradicate the threat from the affected systems. This may involve removing malware, patching vulnerabilities, and restoring systems from backups.
- Recovery: Recover from the incident and restore normal operations. This may involve restoring data from backups, reconfiguring systems, and notifying affected users.
- Lessons learned: Conduct a post-incident review to identify lessons learned and improve the security posture.
Forensics
The forensics process typically consists of the following steps:
- Collection: Collect evidence from the affected systems. This may involve acquiring disk images, memory dumps, and network traffic logs.
- Preservation: Preserve the evidence in a secure and forensically sound manner. This may involve storing the evidence on a read-only medium and maintaining a chain of custody.
- Examination: Examine the evidence to identify and analyze artifacts of interest. This may involve using forensic tools to search for malware, identify compromised accounts, and reconstruct the timeline of events.
- Analysis: Analyze the artifacts of interest to determine the root cause of the incident and the impact on the organization. This may involve identifying the attacker, the attack vector, and the data that was compromised.
- Reporting: Generate a report that documents the findings of the investigation and provides recommendations for preventing future incidents.
Collaboration Between IR and Forensics Teams
IR and forensics teams often collaborate closely to respond to and investigate cybersecurity incidents. For example, IR teams may need to collect and preserve evidence in order to effectively respond to an incident. Similarly, forensics teams may need to work closely with IR teams to understand the context of an incident and to identify the root cause.
Here are some specific examples of how IR and forensics teams may collaborate:
- IR teams may collect evidence from affected systems and then pass it on to forensics teams for analysis.
- Forensics teams may provide IR teams with insights into the attack vector and the attacker’s methods, which can help IR teams to contain and eradicate the threat more effectively.
- IR and forensics teams may work together to develop a recovery plan and to notify affected users.
- IR and forensics teams may also collaborate on post-incident reviews to identify lessons learned and improve the organization’s security posture.
Incident response and forensics are essential components of any cybersecurity strategy. By working together, IR and forensics teams can help organizations to detect, respond to, and recover from cybersecurity incidents more effectively.
#IncidentResponse #Forensics
#Cybersecurity #Protection #BestPractices
#Tips #Recommendations #Collaboration
#Recovery #SecurityAwareness #CyberRisk
#DataProtection #ThreatIntelligence