Voice Cloning: The Emerging Threat of Synthetic Speech
November 15, 2023
Navigating the Digital Age: Staying Ahead of Smishing Scams by
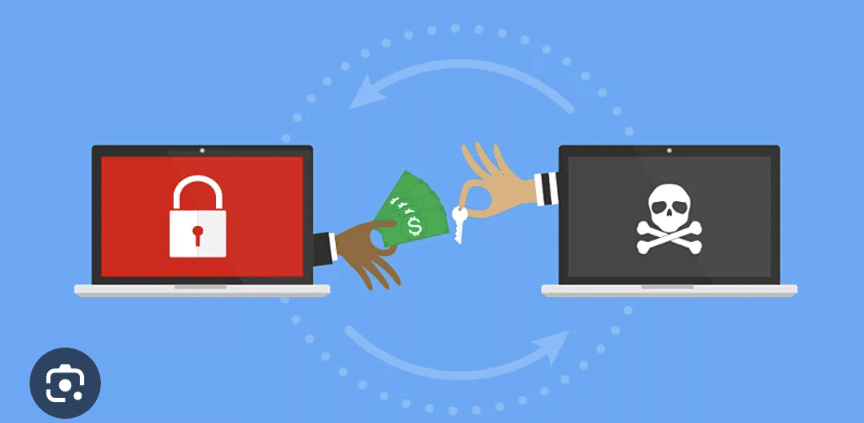
November 17, 2023In the ever-evolving cybersecurity landscape, ransomware has emerged as a formidable threat, wreaking havoc on organizations across industries. While ransomware attacks have traditionally been associated with sophisticated cybercriminals, a recent trend has raised concerns: the increasing involvement of teenagers in orchestrating these attacks.
Citing the ease with which teenagers can acquire powerful hacking tools, Kevin Beaumont, an independent security researcher, expressed his dismay at the alarming rise of ransomware attacks perpetrated by young hackers. He referred to these hacking tools as “digital bazookas,” highlighting their destructive potential and the ease with which they can be employed by individuals with limited technical expertise.
Beaumont’s concerns stem from a recent incident involving a critical vulnerability known as CitrixBleed. This vulnerability, rated with a severity of 9.4 out of 10, exposed session tokens that allowed attackers to bypass multifactor authentication controls within a vulnerable network.
Exploiting this vulnerability, young hackers gained access to the networks of several high-profile organizations, including Boeing, DP World, Industrial and Commercial Bank of China, and Allen & Overy. These attacks demonstrate the significant threat posed by teenagers wielding “digital bazookas,” as they can inflict significant damage on even the most well-defended organizations.
Factors Contributing to the Rise of Teen-Led Ransomware Attacks
Several factors contribute to the increasing involvement of teenagers in ransomware attacks:
- Accessibility of Hacking Tools: The availability of powerful hacking tools on the dark web and other online forums has made it easier for teenagers to acquire the necessary skills and tools to carry out ransomware attacks.
- Financial Motivation: The financial rewards from ransomware attacks can be substantial, providing a lucrative incentive for teenagers seeking quick financial gains.
- Lack of Awareness and Preparedness: Many organizations remain unaware of the evolving tactics and techniques employed by young hackers, making them more vulnerable to their attacks.
- Peer Pressure and Recognition: The online communities where these young hackers operate can foster a culture of peer pressure and recognition, motivating them to engage in these activities.
Mitigating the Threat of Teen-Led Ransomware Attacks
Combating the threat of teen-led ransomware attacks requires a multi-pronged approach that encompasses education, prevention, and response:
- Education and Awareness: Organizations should educate their employees about the evolving tactics and techniques used by ransomware attackers, including those employed by teenagers.
- Vulnerability Management: Organizations should prioritize vulnerability management, promptly addressing newly discovered vulnerabilities to minimize the attack surface that teenagers can exploit.
- Multi-Factor Authentication (MFA): Implementing robust MFA solutions can significantly enhance security by adding an extra layer of protection beyond traditional username and password authentication.
- Data Backup and Recovery: Maintaining regular backups of critical data ensures that organizations can recover quickly from ransomware attacks without succumbing to ransom demands.
- Incident Response Plan: Developing and regularly testing an incident response plan ensures that organizations can effectively respond to ransomware attacks, minimizing downtime and data loss.
The increasing involvement of teenagers in ransomware attacks poses a significant threat to organizations across industries. By understanding the factors contributing to this trend and implementing effective mitigation strategies, organizations can reduce their vulnerability to these attacks and protect their valuable data and assets.
#Cybersecurity #Ransomware #TeenHackers #DigitalBazookas #CyberThreat #DataBreach #ITSecurity #InfoSec #CyberAwareness #Cybercrime