Critical Apple Bug: Understanding the Risks of Root Protection Bypass
January 18, 2025
Connected Cars, Growing Threats: Navigating the Emerging Landscape of Automotive Cybersecurity
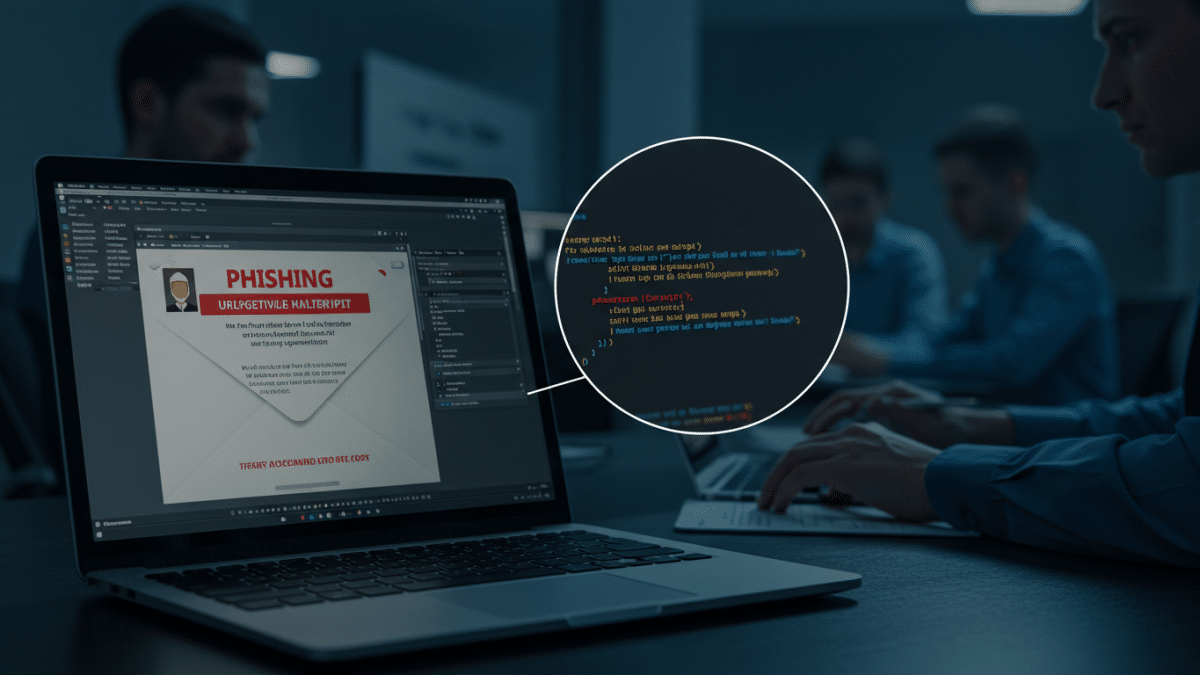
January 23, 2025A newly discovered phishing kit is causing alarm in the cybersecurity world. As reported in the article “New ‘Sneaky 2FA’ Phishing Kit Targets Microsoft 365 Accounts with 2FA Code Bypass,” this kit demonstrates an alarming evolution in phishing tactics, enabling attackers to circumvent two-factor authentication (2FA) protections on Microsoft 365 accounts.
As your trusted cybersecurity partner, Krypto IT is committed to analyzing emerging threats and providing actionable guidance. This blog post will delve into this new “sneaky 2FA” phishing kit, explain how it bypasses 2FA, and outline crucial steps to protect your organization.
Understanding the “Sneaky 2FA” Phishing Kit
This newly discovered phishing kit represents a significant escalation in the sophistication of phishing attacks. While traditional phishing campaigns often rely on stealing passwords alone, this kit is designed to bypass 2FA, a critical security measure that typically adds an extra layer of protection. Here’s how it likely works:
- Targeted Phishing: The attack likely begins with a targeted phishing email designed to look like a legitimate communication from Microsoft or a trusted service. The email may claim that there is an issue with the user’s account or that they need to verify their login credentials.
- Fake Login Page: The phishing email contains a link to a fake Microsoft 365 login page that closely mimics the real one.
- Real-Time Credential and 2FA Code Theft: When the user enters their credentials and 2FA code on the fake login page, the phishing kit intercepts and relays this information to the attacker in real-time.
- Session Hijacking: The attacker can use the stolen credentials and 2FA code to log in to the user’s actual Microsoft 365 account. They then may hijack the legitimate session using a technique like stealing a token that grants them continued access, even if the 2FA code expires.
- Data Exfiltration or Further Attacks: Once inside the account, the attacker can access sensitive data, send phishing emails to other users, or launch further attacks within the organization.
Why This Attack is Particularly Dangerous
- Bypasses 2FA: The kit’s ability to circumvent 2FA is a major concern, as it undermines a widely adopted and effective security measure.
- Steals User Credentials: By intercepting the credentials and 2FA code in real-time, the attacker gains access to the user’s account.
- Highly Convincing: The phishing kit likely uses a high-quality fake login page, making it difficult for users to distinguish it from the real one.
- Targeted Approach: The attack is specifically designed to target Microsoft 365 accounts, which are widely used in businesses and organizations.
Best Practices to Protect Against Advanced Phishing Attacks
This new phishing kit highlights the need for a multi-layered approach to security that goes beyond basic password hygiene and 2FA:
1. Advanced Threat Detection:
- Email Security Gateways: Implement advanced email security gateways that use AI and machine learning to detect sophisticated phishing attacks, including those that attempt to bypass 2FA.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoint activity for suspicious behavior that might indicate a phishing attack or account compromise.
- Security Information and Event Management (SIEM): Use a SIEM system to collect and analyze security logs from various sources, helping to identify and correlate suspicious events.
2. Enhanced Security Awareness Training:
- Regular Training: Conduct regular security awareness training for all employees, emphasizing the importance of recognizing and reporting phishing attempts.
- Phishing Simulations: Use realistic phishing simulations to test employees’ susceptibility to phishing attacks and provide targeted training based on the results.
- Focus on 2FA Bypass Techniques: Educate users about the possibility of 2FA bypass attacks and the importance of remaining vigilant even when using 2FA.
- Verification Procedures: Train employees to independently verify any suspicious requests, especially those involving login credentials or sensitive data, by contacting the supposed sender through a known, trusted channel.
3. Strong Authentication Methods:
- Passwordless Authentication: Consider implementing passwordless authentication methods, such as biometrics or security keys, which are more resistant to phishing attacks.
- Context-Based Authentication: Implement context-based authentication, which analyzes factors like device, location, and user behavior to assess the risk of a login attempt.
4. Web Filtering and Content Inspection:
- Web Filtering: Use web filtering solutions to block access to known phishing websites and other malicious sites.
- Content Inspection: Implement solutions that inspect web traffic for malicious code and scripts.
5. Principle of Least Privilege:
- Restrict User Access: Grant users only the minimum access necessary to perform their job duties. This limits the potential damage if an account is compromised.
6. Incident Response Plan:
- Develop a Plan: Create a detailed incident response plan that outlines procedures for responding to phishing attacks and account compromises.
- Regularly Test the Plan: Conduct drills and tabletop exercises to ensure the plan’s effectiveness.
Company Password Policy Best Practices
While this attack highlights the limitations of passwords, they still play a role in overall security. A strong password policy remains essential:
- Password Complexity:
- Enforce minimum length requirements (at least 12 characters).
- Require a mix of uppercase and lowercase letters, numbers, and symbols.
- Disallow common words or easily guessable information.
- Password Expiration:
- Consider requiring password changes at regular intervals (e.g., every 90-180 days) or when a compromise is suspected.
- Prevent the reuse of old passwords.
- Account Lockout:
- Implement account lockout after a certain number of failed login attempts.
- Multi-Factor Authentication (MFA):
- Mandate MFA for all users, especially those with access to sensitive data or systems.
- Password Storage:
- Never store passwords in plain text.
- Use strong, salted hashing algorithms.
- Employee Training:
- Regularly educate employees on creating strong passwords and the importance of not reusing passwords across different services.
- Encourage or mandate the use of password managers.
Krypto IT: Your Partner in Advanced Threat Protection
The emergence of phishing kits that can bypass 2FA underscores the need for a proactive and multi-faceted approach to cybersecurity.
Krypto IT can help your organization defend against these advanced threats. Our services include: advanced threat detection solutions, security awareness training, phishing simulations, vulnerability assessments, penetration testing, and incident response planning. We can tailor a security solution to your specific needs and industry, helping you build a robust defense against evolving cyber threats.
Contact us today for a free consultation and let us help you protect your organization from sophisticated phishing attacks and other cyber threats.
Don’t let your organization fall victim to advanced phishing. Be proactive. Be prepared. Be secure with Krypto IT.
#Cybersecurity #Phishing #Microsoft365 #2FA #TwoFactorAuthentication #InfoSec #CyberDefense #DataSecurity #ThreatIntelligence #SecurityAwareness #KryptoIT #CyberThreats #BestPractices #PasswordSecurity #EmailSecurity