Beware of BEC Scams This Holiday Season How to Protect Yourself from Holiday Fraud
December 10, 2023
Russia Ramps Up Spear Phishing: A Growing Threat to Global Security
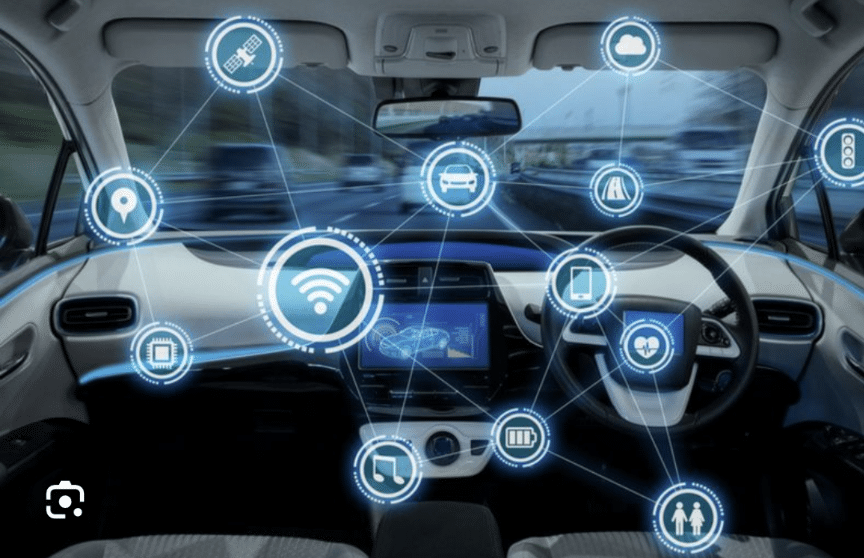
December 13, 2023In today’s tech-driven world, even our vehicles are becoming increasingly connected. Modern cars are equipped with a growing number of features and functionalities, all powered by a network of sensors, software, and internet connectivity. This interconnected ecosystem, while offering undeniable convenience and comfort, also presents a new landscape of cyber vulnerabilities.
Benefits of the Connected Car
The advantages of connected cars are numerous. They can provide:
- Enhanced safety and convenience: Features like autonomous emergency braking, lane departure warning, and adaptive cruise control contribute to safer driving experiences. Additionally, remote diagnostics and connected navigation systems improve convenience and efficiency.
- Personalized driving experiences: Drivers can enjoy personalized music streaming, climate control settings, and even customized driving profiles.
- Enhanced connectivity and entertainment: In-car Wi-Fi, smartphone integration, and advanced entertainment systems offer seamless connectivity and entertainment on the go.
The Dark Side: Cybersecurity Vulnerabilities
The interconnectedness of modern cars opens doors to cyberattacks, posing potential risks to drivers, passengers, and even personal data privacy. Here are some key vulnerabilities:
- Software vulnerabilities: Complex software systems in connected cars often contain vulnerabilities that hackers can exploit to gain unauthorized access. This could allow them to take control of critical systems like steering, brakes, and even remotely unlock the car.
- Unsecure communication protocols: Data communication between the car’s internal systems and external networks can be susceptible to interception or manipulation if not properly secured. This could expose sensitive information or allow hackers to inject malicious commands.
- Weak authentication and authorization systems: Insufficiently robust authentication and authorization mechanisms can enable unauthorized users to access and manipulate car functions. This could lead to serious safety threats or data breaches.
- Physical attacks: Vulnerable physical interfaces like USB ports or diagnostic connectors can be exploited by attackers to gain access to the car’s internal network.
Real-World Examples
Recent incidents have highlighted the potential dangers of connected car vulnerabilities. In 2015, researchers remotely hacked a Jeep Cherokee, demonstrating control over its steering, acceleration, and brakes. Similarly, hackers have exploited vulnerabilities in keyless entry systems to steal cars remotely.
Potential Consequences of Attacks
A successful cyberattack on a connected car can have serious consequences:
- Physical harm: Hackers could gain control of critical systems, leading to accidents or even fatalities.
- Financial loss: Hackers could access and steal personal information like credit card details or financial records from car systems.
- Privacy violations: Personal data collected by the car, such as location tracking and driving habits, could be exposed or used for malicious purposes.
Protecting Our Connected Future
The increasing security concerns surrounding connected cars necessitate proactive measures to mitigate risks. Here are some essential steps:
- Stronger cybersecurity standards: Governments and industry players need to collaborate to develop and implement robust cybersecurity standards for connected cars.
- Regular software updates: Manufacturers should prioritize timely software updates to patch vulnerabilities and ensure the latest security measures are in place.
- Improved user awareness: Drivers should be educated about the potential risks and provided guidance on how to protect their cars from cyberattacks.
- Enhanced security protocols: Secure communication protocols and robust authentication and authorization systems must be implemented to safeguard data and prevent unauthorized access.
- Focus on physical security: Physical interfaces like USB ports and diagnostic connectors should be adequately secured to prevent them from becoming attack vectors.
The Path Forward
The connected car revolution is undeniably here to stay. While it offers significant benefits, ensuring the safety and privacy of drivers remains paramount. By addressing cybersecurity vulnerabilities through collaborative efforts and continuous improvements, we can navigate this technological landscape responsibly and ensure a safe and secure future for connected cars.
Additional Considerations:
- The ethical implications of data collection and usage in connected cars need careful evaluation and robust data privacy regulations.
- Collaboration between car manufacturers, cybersecurity experts, and government agencies is crucial to develop comprehensive security solutions.
- Continuous research and development are essential to stay ahead of ever-evolving cyber threats and vulnerabilities.
By embracing a proactive approach to cybersecurity, we can unlock the full potential of connected cars while safeguarding against the potential risks, paving the way for a safer and more connected future of mobility.
#connectedcar #cybersecurity #vulnerability #privacy