The latest version of the fake browser update scam: What you need to know
October 20, 2023
Your Mobile Device is a Cybercriminal’s Dream Target – Here’s How to Fight Back
October 23, 2023Third-party risk management (TPRM) is the process of identifying, assessing, and mitigating risks associated with third-party vendors. Third-party vendors can include suppliers, contractors, service providers, and other businesses that an organization relies on to operate.
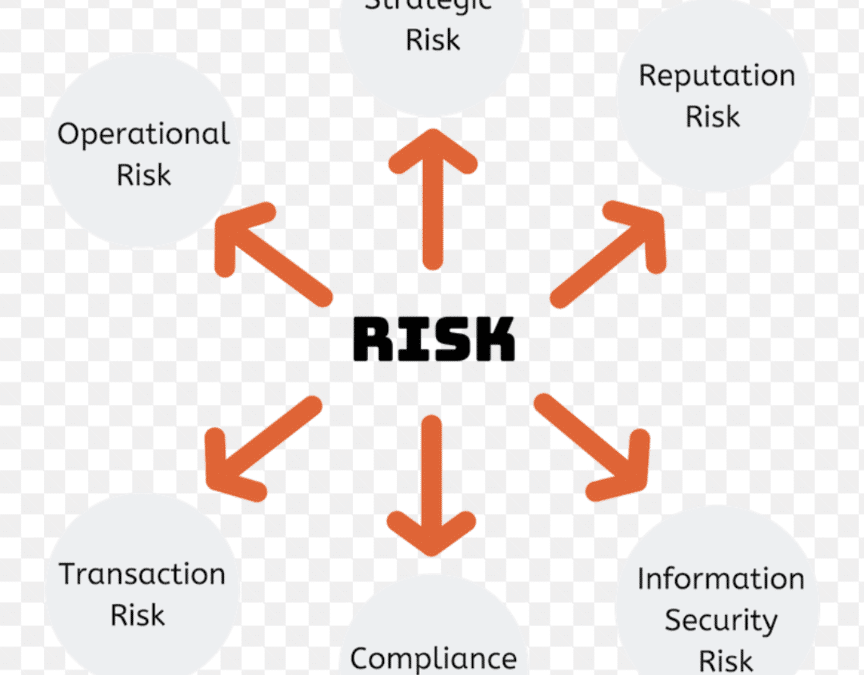
TPRM is important because third-party vendors can introduce a variety of risks to an organization, including:
- Cybersecurity risks: Third-party vendors may have access to sensitive data or systems, and a breach at a third-party vendor could have a significant impact on the organization.
- Financial risks: If a third-party vendor fails, it could disrupt the organization’s operations and lead to financial losses.
- Compliance risks: Third-party vendors may be subject to regulations that the organization must also comply with. If a third-party vendor fails to comply with these regulations, it could put the organization at risk of fines and other penalties.
To effectively manage third-party risk, organizations should implement a comprehensive TPRM program. This program should include the following steps:
- Identify third-party vendors: The first step is to identify all of the third-party vendors that the organization relies on. This includes vendors of all sizes, from small businesses to large enterprises.
- Assess risks: Once the third-party vendors have been identified, they need to be assessed in terms of the risks they pose to the organization. This assessment should consider factors such as the vendor’s size, industry, and the types of services they provide.
- Mitigate risks: Once the risks have been assessed, the organization needs to implement controls to mitigate those risks. This may involve implementing security requirements for vendors, conducting vendor audits, and purchasing insurance to protect against financial losses.
- Monitor risks: The TPRM program should be monitored on an ongoing basis to ensure that it is effective and that new risks are identified and mitigated.
Here are some additional tips for effective TPRM:
- Develop a risk-based approach: The TPRM program should be tailored to the specific risks that the organization faces. Organizations should prioritize their TPRM efforts on the vendors that pose the highest risk.
- Involve stakeholders across the organization: TPRM is not just the responsibility of the IT department. It is important to involve stakeholders from across the organization, such as procurement, finance, and legal, in the TPRM process.
- Use technology to automate tasks: There are a variety of technology solutions that can help to automate tasks associated with TPRM, such as vendor risk assessments and vendor monitoring.
- Continuously improve the program: The TPRM program should be continuously improved to ensure that it is effective and up-to-date.
Additional information:
Here are some of the key challenges of TPRM:
- Lack of visibility: It can be difficult for organizations to track all of their third-party vendors and the risks they pose. This is especially true for large organizations with complex supply chains.
- Vendor resistance: Some vendors may be resistant to complying with the organization’s TPRM requirements. This is especially true if the requirements are burdensome or costly.
- Resource constraints: TPRM can be a resource-intensive process. Organizations need to have the resources to implement and maintain a comprehensive TPRM program.
Despite these challenges, TPRM is an essential part of any organization’s risk management strategy. By implementing a comprehensive TPRM program, organizations can reduce the risks associated with third-party vendors and protect their IT systems, data, and customers.
TPRM is an important process for all organizations, regardless of size or industry. By implementing a comprehensive TPRM program, organizations can reduce the risks associated with third-party vendors and protect their IT systems, data, and customers.
#ThirdPartyRiskManagement #TPRM #CyberSecurity #RiskManagement #Compliance #ComplianceRisk #FinancialRisk #InformationSecurity #VendorRisk #VendorManagement